
Many individuals might not consider that an ordinary USB cable could pose a risk. In essence, this basic USB cord serves only as a link between gadgets, appearing harmless enough within the realm of technology. However, beneath its innocuous exterior lies potentially far greater dangers than one might anticipate. All USB-C cables are not created equal. As technology shrinks, it becomes easier to conceal wireless components like additional radio transmitters and miniaturized chips virtually anywhere. This opens up numerous opportunities for cybercriminals, governmental surveillance units, and similar organizations to exploit cables and tiny devices as entry points.
Over the last several years, particularly within the past ten years, many instances of hidden microchips and even explosive materials being found inside various electronic devices such as cellphones, pagers, servers, and an array of hardware components have come to light. Although most of these incidents involve actions taken by entities linked to governments, they often target relevant adversaries. It’s crucial to stay informed about how contemporary technology can be exploited for malicious purposes. In this piece, therefore, we will examine some alarming examples of covert implants identified in ordinary-looking equipment and wiring.
Read more: 10 Overlooked Automotive Gadgets You Should Consider for Your Ride
USB cables can include much more than you might imagine.
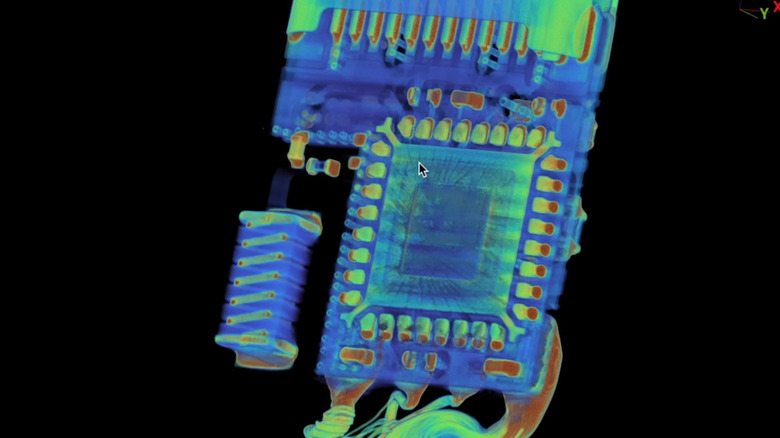
It’s unlikely you’ve considered using 3D scanning for your USB cables. Nevertheless, apart from slicing them open—which would ruin them—that could be the most effective method to uncover any hidden malevolent components inside. Experts have verified that it’s feasible to incorporate harmful devices into USB wires without detection, except through a detailed three-dimensional examination.
The particular cable under discussion was the O.MG USB-C cable When a manufacturing solutions company Lumafield When the O.MG cable underwent a CT scan, investigators discovered a radio antenna, a microcontroller, and an additional circuit board. These components enable the injection of various payloads into devices, such as simulated keyboard inputs and mouse actions, along with conducting keylogging and geofencing attacks, amongst other alarming uses. However, before you become overly concerned, remember that this cable was not attempting to appear harmless. Instead, it serves as a sophisticated device designed specifically for red-team exercises, priced at over $120 when last reported, and promoted primarily for educational and field study objectives. That being said, should anyone aim to present it to you as a standard USB cable, chances are high that you would fail to recognize its true nature.
To make things clear, you shouldn’t feel compelled to send each cable you purchase off for laboratory testing. Provided that you’re acquiring a high-quality cable from a trustworthy vendor, the likelihood of receiving one that has been interfered with is extremely low. Adding additional elements to a cable demands both funds and technical know-how, which probably wouldn't be squandered on targeting an average individual. Should you wish to implement some safety measures, the company behind the O.MG cable offers complementary products. malicious cable detector that illuminates when something out of the ordinary is picked up.
Pagers to servers have been tampered with by malicious entities.

Your mobile device or another piece of technology might carry harmful software as well, and over the last several years, we've seen numerous instances where devices were covertly compromised for nefarious reasons. The most recently publicized event occurred in September 2024 when an Israeli intelligence mission resulted in dozens of fatalities. The New York Times Israeli agents established a dummy corporation for producing numerous pagers and walkie-talkies embedded with remote explosives. These compromised communication tools were disseminated across Lebanon and Syria among individuals believed by Israel to have ties to the extremist organization Hezbollah. The assault unfolded in phases: initially, the pagers buzzed, leading recipients to bring them close to their ears as though responding to an actual call. Consequently, when detonated moments later, these explosions inflicted maximum harm. Thirty-two lives were lost, notably including a young girl of nine years old who responded to her father’s pager. Additionally, thousands sustained injuries from this incident.
Many individuals probably do not need to worry about experiencing another violently aggressive assault. Spying activities are much more probable. For instance, in October 2018, Bloomberg it was reported that China had embedded microchips, smaller than a grain of rice, into servers manufactured by Super Micro. This discovery set off concerns throughout the United States because the company’s equipment was utilized by entities such as Apple, Amazon, and the Department of Defense. Nonetheless, Apple and Amazon criticized Bloomberg For the report, requesting a retraction, Subsequently, Super Micro issued an independent review. The search did not uncover any such spyware. On the other hand, China’s intelligence agencies have reportedly discovered hidden spy equipment camouflaged as USB flash drives and various gadgets, according to reports from Chinese state-run media outlets. Global Times In August 2024, and there will be at least one Chinese phone with possible malicious software has raised concern.
Interested in staying updated with the newest technology and automotive developments? Sign up for our complimentary email newsletter. For the most recent news stories, detailed guides, and step-by-step advice, delivered once per email.
Read the original article on Wiseova .


0 Comments